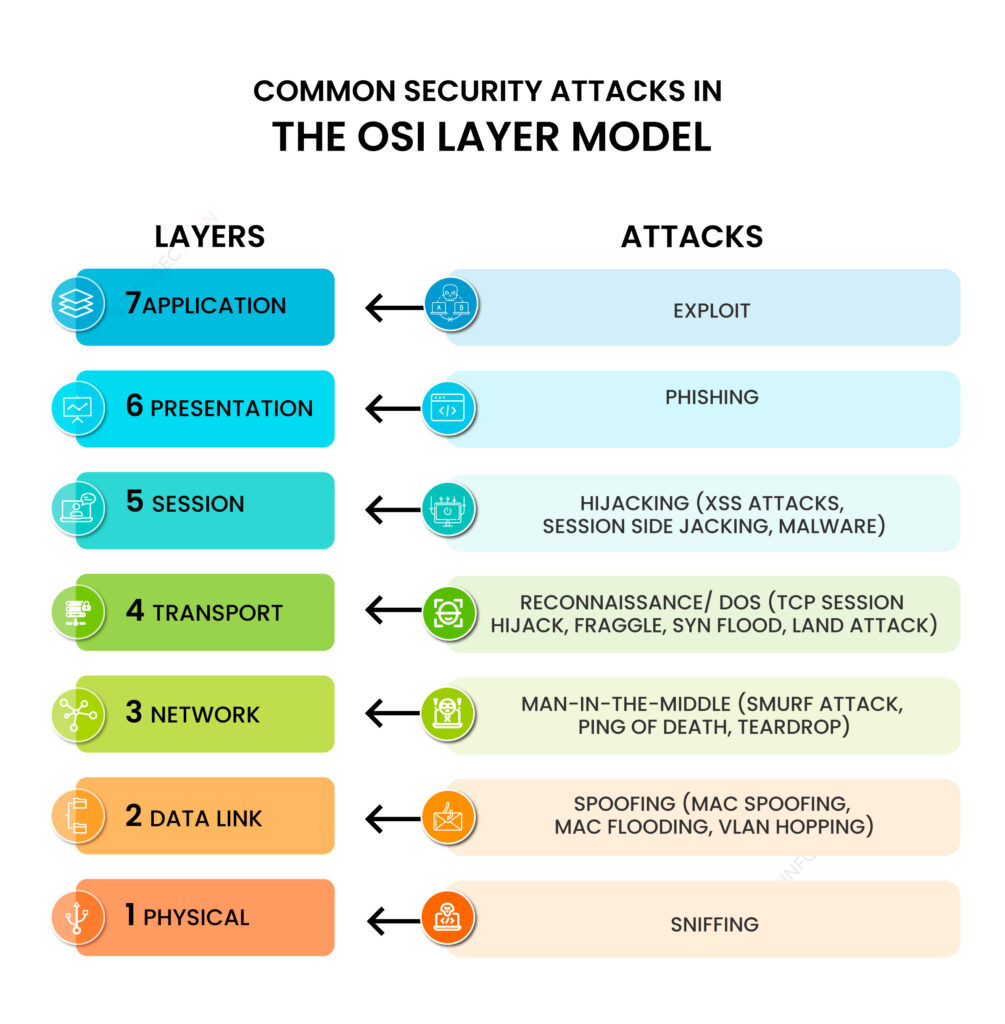
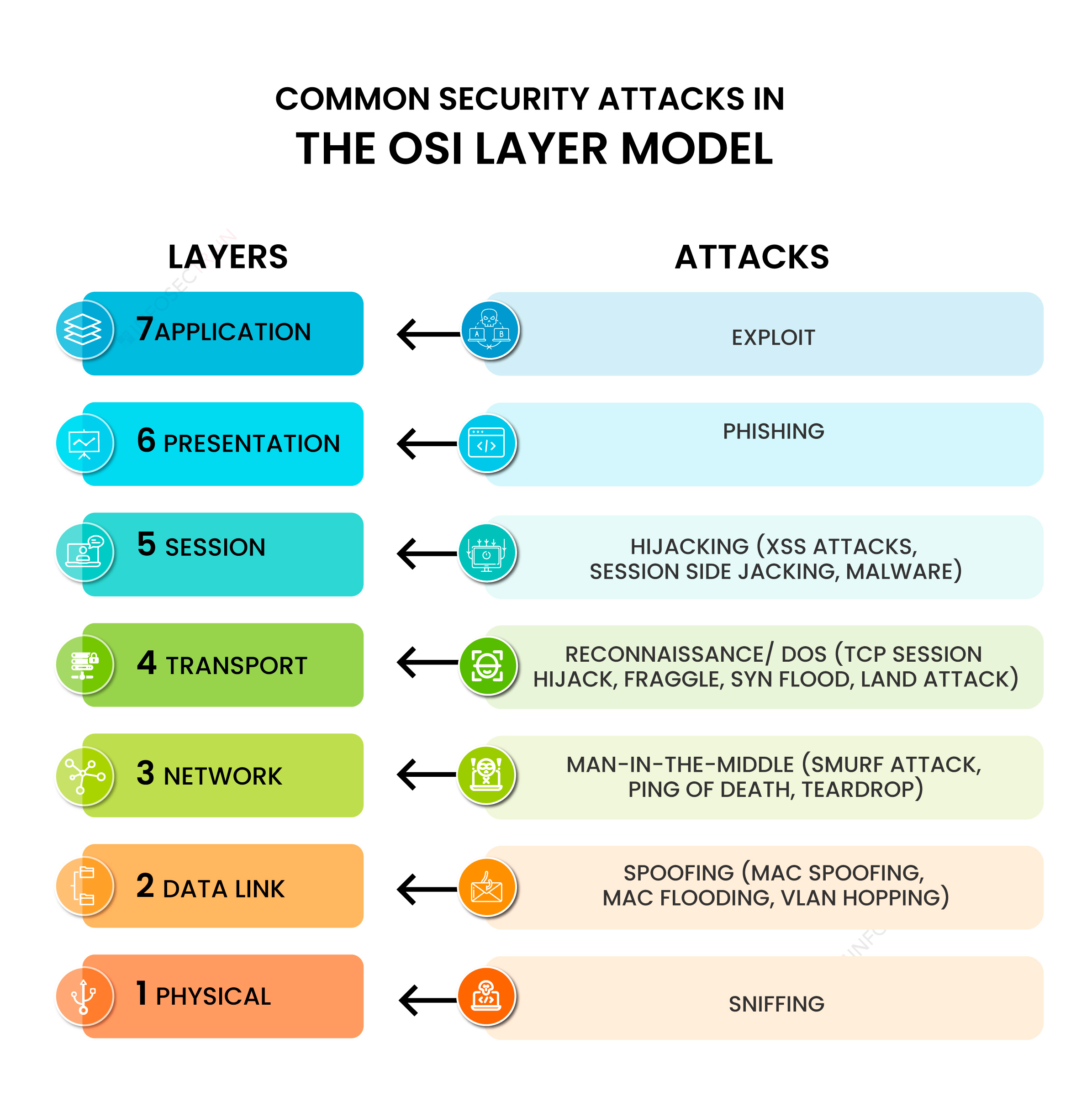
1) Sniffing attacks consist of intercepting data using a packet sniffer application. Then, if the captured packets are not encrypted, the packet sniffer can be used to read them. This allows attackers to analyze the network and gain information to corrupt it or even cause it to crash.
2) Spoofing attacks consist of a person or program falsifying data to identify as an authorized user or device. By impersonating authorized users or devices, attackers can bypass access control to systems, steal data and spread malware.
3) Man-in-the-middle attacks, abbreviated as “MitM attacks”, consist of an attacker placing himself between two communicating parties to monitor, relay and even alter the content of messages.
4) Reconnaissance attacks consist of gathering information about a system in order to identify its vulnerabilities. Although it was originally used as an ethical hacking technique to identify security loopholes and improve security, it has also become a mechanism to identify vulnerabilities before launching a cyberattack.
5) Hijacking attacks consist of intercepting and taking control of an established communication session either to access sensitive data or to gain unauthorized access to the targeted user’s computer or account.
6) Phishing attacks consist of deceiving individuals into revealing sensitive data through diverse techniques. It is one of the most commonly used cyberattacks nowadays and includes many types of attacks.
7) An exploit consists of taking advantage of vulnerabilities in software applications to gain unauthorized access and take control over a system, and perform diverse types of attacks, such as a denial-of-service attack.