5 Urgent Cyber Security Trends in 2024

Trend 1: 90% of phishing websites are live for just one day Attackers create and dismantle phishing sites quickly, often targeting high-traffic events, like holidays or significant product launches, maximizing their chances of success in a short window. The ephemeral strategy makes traditional security measures less effective, as many detection systems rely on historical data […]
Vodafone & Google Announce Partnership focused on AI, Cloud & Cyber Security!

Vodafone and Google have just announced a groundbreaking Ten-Year Partnership expansion, valued at over $Billion, to focus on AI-Powered Services, Devices & Enhanced TV Experiences for Millions of Users across Europe & Africa. This collaboration leverages Google Cloud & Google’s Gen AI Gemini models to drive digital transformation for Consumers & Businesses across 15 Countries. […]
Cyber Allies – Choosing The Right MSSP

Selecting the right Managed Security Service Provider (MSSP) is a pivotal decision for organisations seeking to bolster their Cyber Security Defences. In this Episode, we explore the Key Considerations & Strategic Approaches to ensure you choose an MSSP that aligns seamlessly with your unique security needs and overarching business objectives. Understanding Your Security Needs: Identifying […]
MSSPs: Cyber Allies – Choosing The Right MSSP

Selecting the right Managed Security Service Provider (MSSP) is a pivotal decision for organisations seeking to bolster their Cyber Security Defences. In this Episode, we explore the Key Considerations & Strategic Approaches to ensure you choose an MSSP that aligns seamlessly with your unique security needs and overarching business objectives. Understanding Your Security Needs: […]
Top 5 Regulatory Changes Shaping Cyber Security in 2024

As the Regulatory environment becomes increasingly stringent, the importance of being prepared for these changes cannot be overstated. Failure to comply with New Regulations can result in severe financial penalties, reputational damage and increased vulnerability to Cyber Threats. Proactive measures and timely compliance are not just Regulatory necessities; they are essential to safeguarding your organisation’s […]
How the New Cyber Security Bill Will Strengthen UK Business Defences

How the New Cyber Security Bill Will Strengthen UK Business Defences – The Government Unveils New Data & Cyber Security Legislation in King’s Speech! In a Landmark Announcement, the Government has unveiled the new Cyber Security & Resilience Bill as part of the King’s Speech. This Legislation comes in response to the escalating Cyber Threats […]
The Government Unveils New Data & Cyber Security Legislation in King’s Speech!

King Charles’s Speech yesterday the Introduction of the Cyber Security & Resilience Bill. This Bill aims to Enhance the UK’s Defenses against Cyber Threats by Establishing Stringent Regulations & Improving the Resilience of Critical Infrastructure. Cyber Security & Resilience Bill: Our Digital Economy is increasingly being attacked by Cyber Criminals & State Actors, affecting […]
Cyber Security Insights – Ransomware Defence Strategies in 2024

Ransomware has emerged as an insidious and relentless adversary in today’s digital landscape, leaving Individuals & Organisations grappling with the devastating consequences of their attacks. These malicious threats are designed to encrypt critical data and extort payment for its release, and over the years, they’ve evolved into increasingly sophisticated and disruptive forms. As we delve […]
Cyber Security Insurance Rates Fall as Businesses Improve Their Security

Cyber insurance premiums are falling globally as businesses become more adept in curbing their losses from cyber crime. Insurance premiums to protect companies against cyber attacks rocketed in 2021 and 2022, as the COVID-19 pandemic drove cyber incidents. But premiums have been dropping in the past year. The cyber insurance market saw double digit price […]
7 Common Security Attacks in The OSI Layer Model
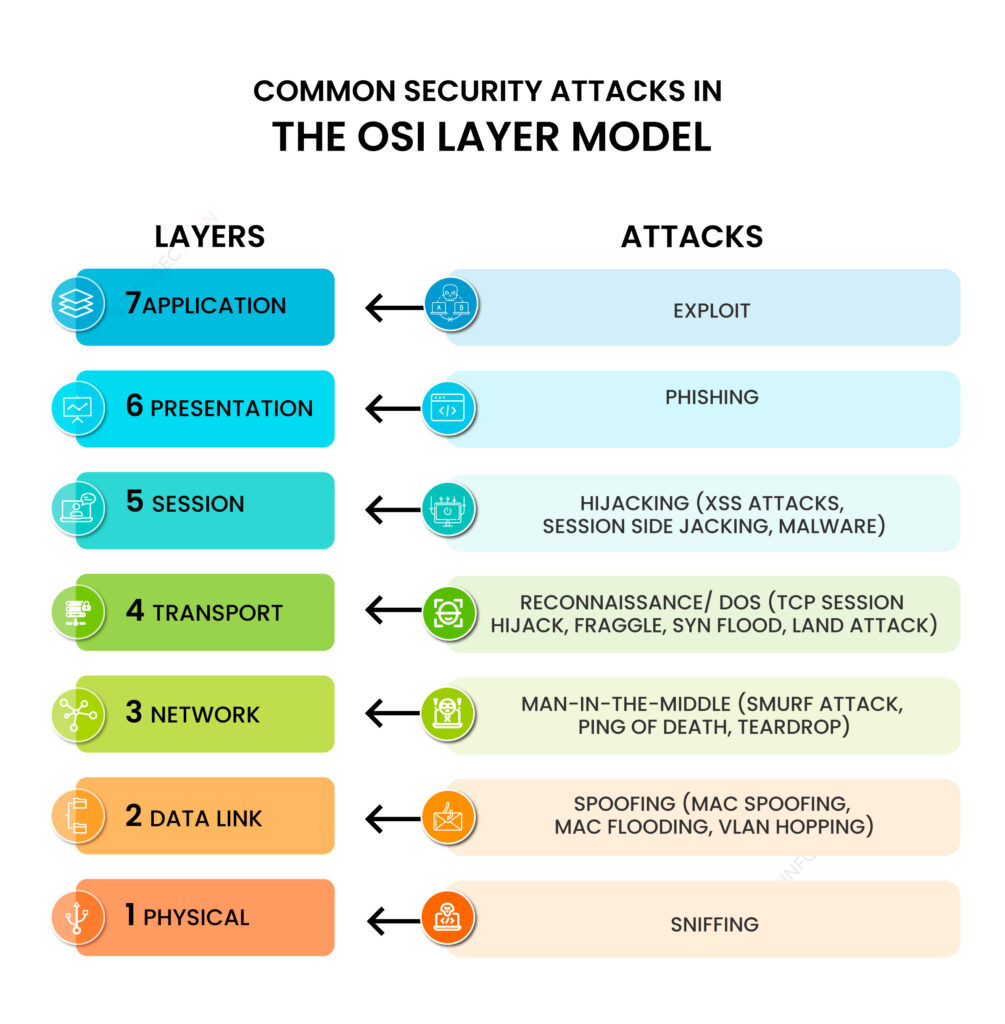
1) Sniffing attacks consist of intercepting data using a packet sniffer application. Then, if the captured packets are not encrypted, the packet sniffer can be used to read them. This allows attackers to analyze the network and gain information to corrupt it or even cause it to crash. 2) Spoofing attacks consist of a person or […]




